Research
NPM Package Confusion
In this article I will demonstrate how an organization exposed themselves to an NPM package takeover. Vulnerability:...
Analysis of Malicious Phishing Email
A while back I worked an incident for a company which stemmed from a phishing email. When I start working incidents...
CSRF to Account Takeover
My wife and I are regulars at a popular boutique fitness studio which, as all things must, comes with a web app. So...
Adversary Levels
1. Level 1 – Common Adversary: This level of adversary is the lowest level tier. Most adversaries at this level are...
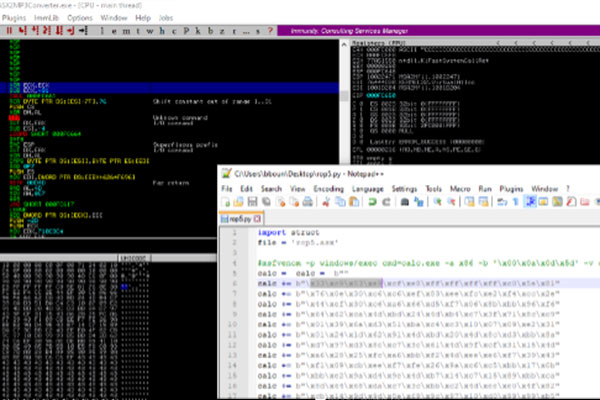
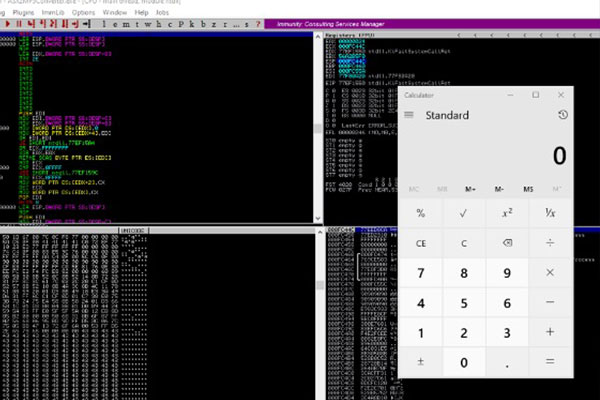
ASX to MP3 Converter Buffer Overflow with DEP Bypass – ROP Chains
First we can use mona.py to identify gadgets and compute potential rop chains..<snip>..Check mona’s output...
ASX to MP3 Converter Buffer Overflow
Upon opening the provided exploit file, fuzzing.asx in Notepad++ it’s clear there is some sort of file formatting...
Bug Bounty
There are countless resources out there on participating in Bug Bounty programs from a researcher's perspective....