
by Diffie Shellman | Aug 20, 2024 | Supply Chain
In this article I will demonstrate how an organization exposed themselves to an NPM package takeover. Vulnerability: Dependency Confusion Impact (In increasing order of severity): An attacker can submit unauthorized code into the victim’s software development...

by Diffie Shellman | Aug 13, 2024 | Malware Analysis
A while back I worked an incident for a company which stemmed from a phishing email. When I start working incidents with a clear entry point I always enjoy analyzing the malware for a variety of reasons. As it pertains to recovery, it’s an excellent way to begin...

by Diffie Shellman | Aug 9, 2024 | Web Apps
My wife and I are regulars at a popular boutique fitness studio which, as all things must, comes with a web app. So naturally I decided to take a look under the hood to see what sort of trouble I could get into. In this case I was already looking for Cross-Site...

by Diffie Shellman | Jan 25, 2023 | Enterprise Operations
1. Level 1 – Common Adversary: This level of adversary is the lowest level tier. Most adversaries at this level are not directly targeting an organization but aiming to attack any easy target or organization. This adversary utilizes basic and free tools with little...
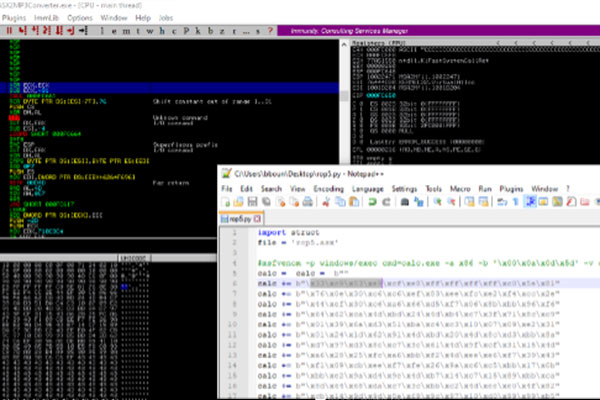
by Diffie Shellman | Jan 25, 2023 | Exploit Development
First we can use mona.py to identify gadgets and compute potential rop chains ..<snip>.. Check mona’s output directory for following files Opening rop_chains.txt will provide an extensive list of rop chains that could potentially be used to bypass DEP. In this...




