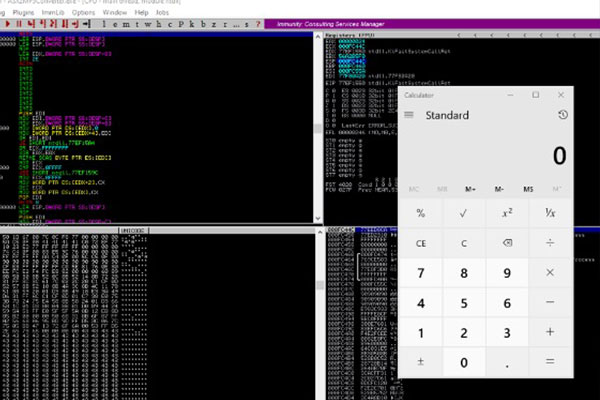
by Diffie Shellman | Jan 25, 2023 | Exploit Development
Upon opening the provided exploit file, fuzzing.asx in Notepad++ it’s clear there is some sort of file formatting taking place. Opening up the same file using Wordpad reveals that this is merely a text file and the payload is simply a large string passed in as an HTTP...

by Diffie Shellman | Jan 25, 2023 | Enterprise Operations
There are countless resources out there on participating in Bug Bounty programs from a researcher’s perspective. However, there are a surprisingly few number of resources on how to launch and maintain a program in an enterprise ecosystem. Whether you’ve...

by Diffie Shellman | Jan 24, 2023 | Enterprise Operations
So you want to launch an engagement at your organization to simply…find vulnerabilities but you have many questions, and you have questions about your questions, and then there are questions you don’t even know to ask. Where and how do you start? What is your...

by Diffie Shellman | Jan 17, 2023 | Enterprise Operations
1. Technical Assessment (Generic Adversary Model): Focus is on technology without an adversary model. Examples include running vulnerability scanning tools or even other generic off the shelf tools to identify weaknesses in the environment. This would include...





